Multiple CodeQL scans performed
Question
What does the CodeQL scan issue “Multiple CodeQL scans performed” mean and how can I detect it?
Answer
There are multiple methods that may be used to perform a CodeQL scan. For example, the default GitHub CodeQL may be performed, a scan may be performed through one or more workflows, or the results of a scan in a CI/CD pipeline can be uploaded into GitHub. These are referred to as setup types in the GitHub GUI.
This scan issue indicates that either multiple setup types or multiple action workflows have been used to create CodeQL scans which can lead to inconsistencies between scans.
How to detect multiple setup types
The following steps may be taken to determine when multiple different CodeQL scans were performed:
-
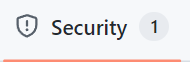
Navigate to your application’s GitHub repository and select the “Security” tab:
-
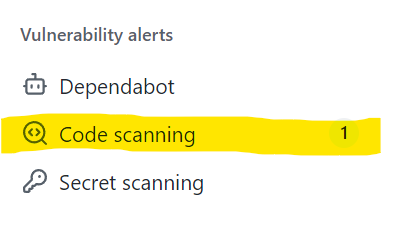
On the left-hand side of the “Security overview” page will be a section showing the number of open vulnerability alerts. Select the “Code scanning” menu item to view the alerts:
-
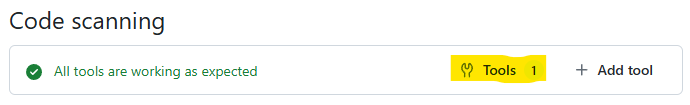
Near the top of the page is the Tool Status bar. Select the “Tools” button:
-
You should now see a CodeQL page that shows “Scanned files” and “Setup types”. Click on the “Setup type”. If there is more than one as shown below, this is an issue:
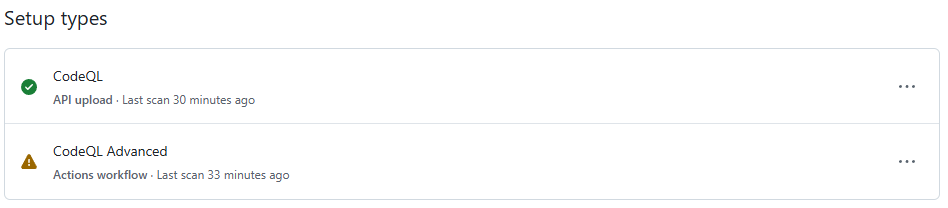
How to detect multiple action workflows
The following steps may be taken to determine when multiple different workflows are performing CodeQL scans:
-
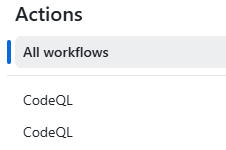
Navigate to your application’s GitHub repository and select the “Actions” tab:
-
On the left hand side of the screen will be a list of all action workflows. If more than one workflow is active and running CodeQL, this is an issue.