How to get started drawing application threat model diagrams
Question
How do I get started drawing an application threat model diagram using Microsoft Threat Modeling Tool?
Answer
VA application developers will start the threat modeling by creating an application threat model diagram using the Microsoft Threat Modeling Tool. The diagrams generally cannot be created in an automated fashion, so it is useful to start modeling from a notional example. Sample application threat model diagrams may be requested from the OIS Software Assurance Office.
Another way to get from for example lists of technologies to a Microsoft Threat Modeling Tool diagram is to find notional diagrams depicting common uses of those technologies, that can perhaps then be tailored to reflect your application’s design. This approach can be helpful in overcoming artist’s block caused by starting from a blank page.
Examples of types of notional diagrams that are generally helpful from a threat model diagram perspective include:
- Application architecture diagrams (e.g. mobile app, web application, etc.)
- Design patterns implemented (e.g. Model-View-Controller, Model-View-Presenter, etc.)
For example, if the application in question is a C# application, asking which of the these architectures most closely resembles it, and perhaps also asking which of these design patterns the application implements. A Model-View-Presenter (MVP) design pattern implemented in C# for example can be depicted as three generic process elements.
Application-specific architectural elements can then be added to the diagram along with interactions between for example databases and the model element, etc. Adding trust boundaries and tailoring the diagram can then continue iteratively in that fashion. An example of this process is depicted in the figure below.
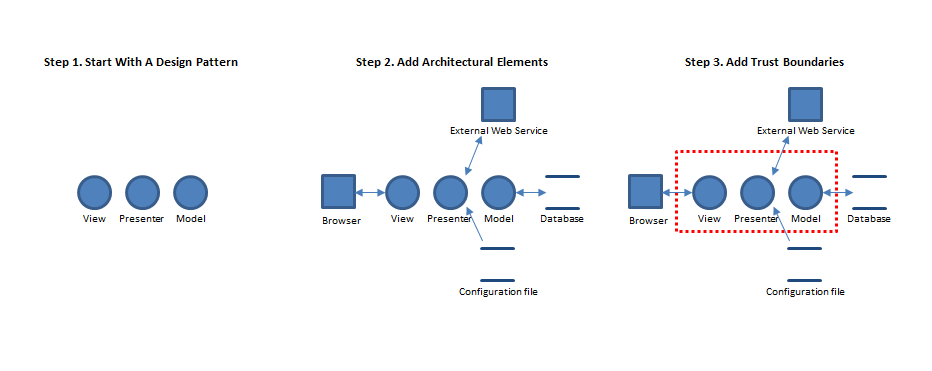
This approach, coupled with investigating clues such as off-hand mention of security features or application components mentioned in available documentation, can then be the starting point for corresponding Microsoft Threat Modeling Tool diagram elements.
Additional examples of notional diagrams that may be helpful to readers of this technical note can be found below.
Additional Architecture And Design Pattern Diagram References
Additional examples of notional diagrams include the following:
| Language | Type of Diagram | Location | Notes |
|---|---|---|---|
| ASP.NET, VB.NET, C# (.NET) | Application architectures | example | For multiple application types |
| ASP.NET, VB.NET, C# (.NET) | Application architectures | example | For Windows services |
| ASP.NET, VB.NET, C# (.NET) | Application architectures | example 1 example 2 | For broker architectural pattern |
| ASP.NET, VB.NET, C# (.NET) | Design patterns | example | For web applications |
| ASP.NET, VB.NET, C# (.NET) | Design patterns | example | For ASP.NET MVC framework (provides an alternative to the ASP.NET Web Forms pattern [MVP])See also this reference [..]In the MVC, the Controller is responsible for determining which View is displayed in response to any action including when the application loads. This differs from MVP where actions route through the View to the Presenter. In MVC, every action in the View correlates with a call to a Controller along with an action [..] One other big difference about MVC is that the View does not directly bind to the Model. The view simply renders, and is completely stateless. In implementations of MVC the View usually will not have any logic in the code behind. This is contrary to MVP where it is absolutely necessary because, if the View does not delegate to the Presenter, it will never get called [..]" |
| ColdFusion CFML | |||
| Java (including Android) | Design patterns | example 1 example 2 example 3 example 4 | |
| Java (including Android) | Design patterns | example 1 example 2 | For Spring Web MVC |
| JavaScript/AJAX | Design patterns | example 1 example 2 example 3 | For SOA |
| JSP | |||
| Objective-C/C++ | |||
| PHP | |||
| Ruby | |||
| Swift | |||
| Visual Basic |